Thales, a leader in critical information systems, cybersecurity and data security, announced the results of its 2017 Thales Data Threat Report, issued in conjunction with analyst firm 451 Research. 68% of respondents have experienced a breach with 26% experiencing a breach in the last year – both numbers that rose from last year. Paradoxically, overall security spending is also up. In 2017 73% of organisations increased IT security spending, a marked jump from 2016 58%.
The report, which is in its fifth year, polled 1,100 senior IT security executives, at large enterprises around the world and indicates an ongoing disconnect between the security solutions organisations spend money on and the ability of those solutions to protect sensitive data. While 30% of respondents classify their organisations as very vulnerable or extremely vulnerable to data attacks and the number of breaches continues to rise, the two top spending priorities are network 62% and endpoint 56% protection solutions. Counter-intuitively, spending on data-at-rest solutions 46% comes last.
Garrett Bekker, Senior Snalyst, Information Security at 451 Research and author of the report says: “One possible explanation for this troubling state? Organisations keep spending on the same solutions that worked for them in the past but are not necessarily the most effective at stopping modern breaches. Data protection tactics need to evolve to match threats. It stands to reason that if security strategies are not equally as dynamic in this fast-changing threat environment, the rate of breaches will continue to increase.”
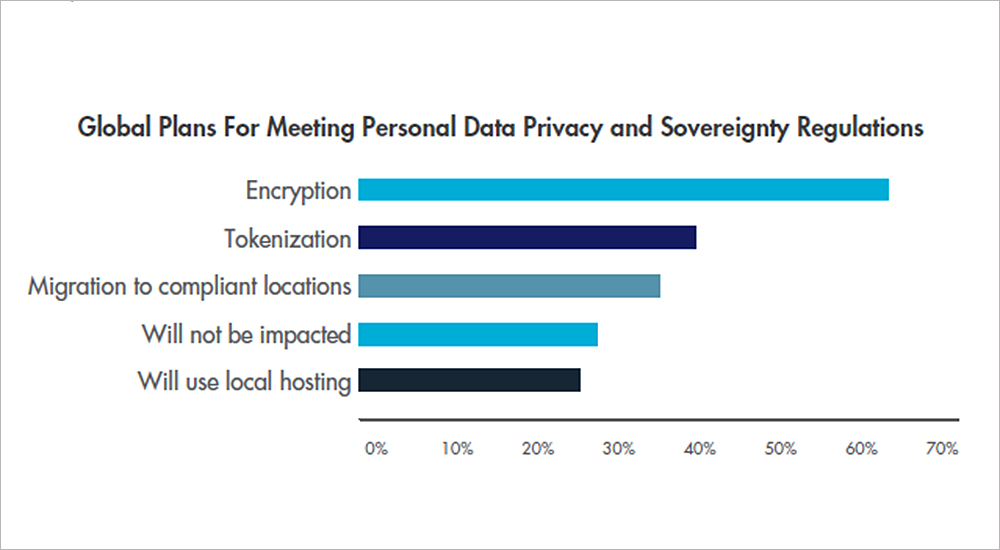
The reasons behind security spending decisions are varied, but the key driver remains constant: compliance. Almost half 44% of respondents list meeting compliance requirements as their top spending priority, followed by best practices 38% and protecting reputation 36%. 59% also believe compliance is very or extremely effective at preventing data breaches. While compliance regulations provide a data security blueprint, they are by no means the only consideration when building a security strategy robust enough to withstand sophisticated attackers.
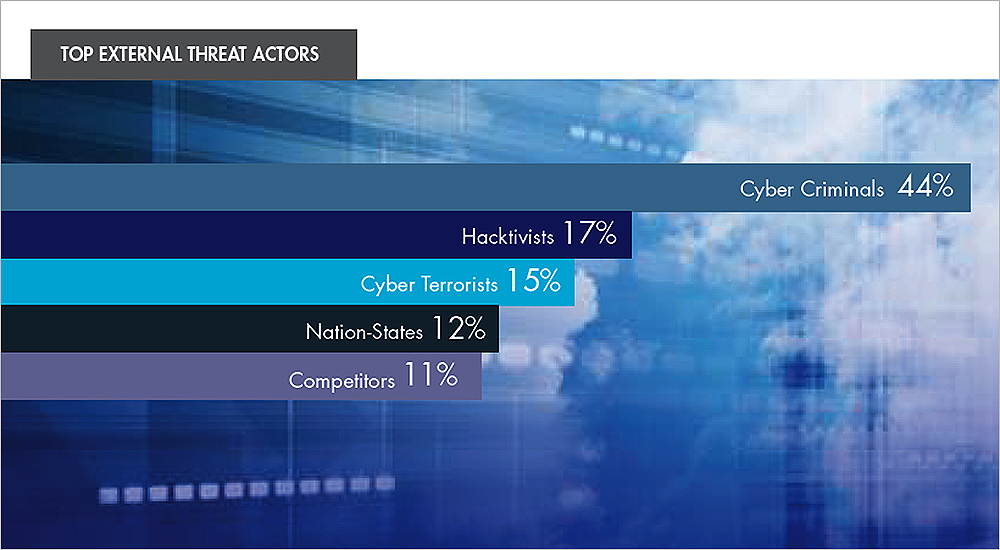
As in years past, the 2017 Data Threat Report explored threat perceptions. All vertical industries polled identified cyber criminals as the top threat 44%, followed by hacktivists 17%, cyberterrorists 15% and nation-states 12%. With respect to internal threats, 58% of respondents believe privileged users are the most dangerous insiders a slight decrease from last year’s 63%. At 44%, executive management is seen as the second-most-risky insider, followed by ordinary employees 36% and contractors 33%.
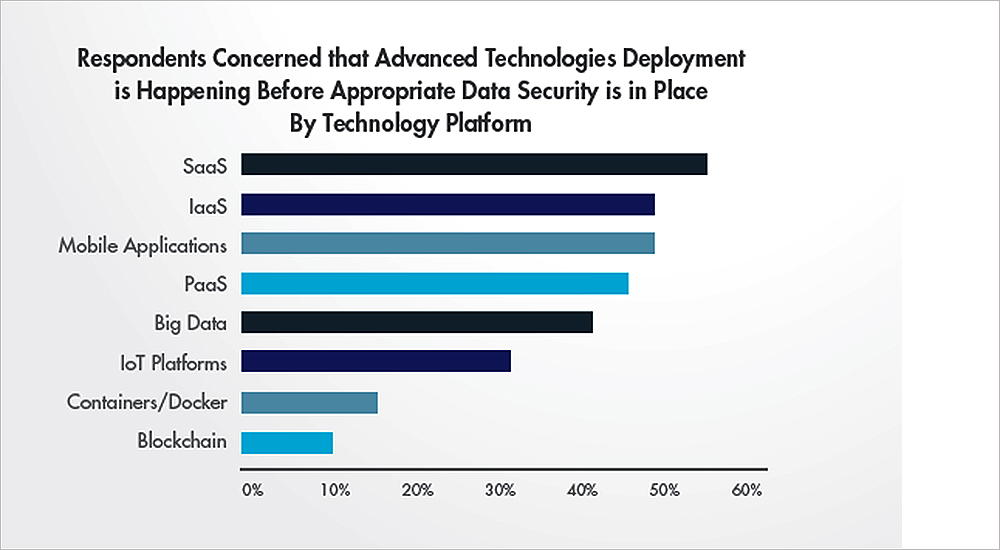
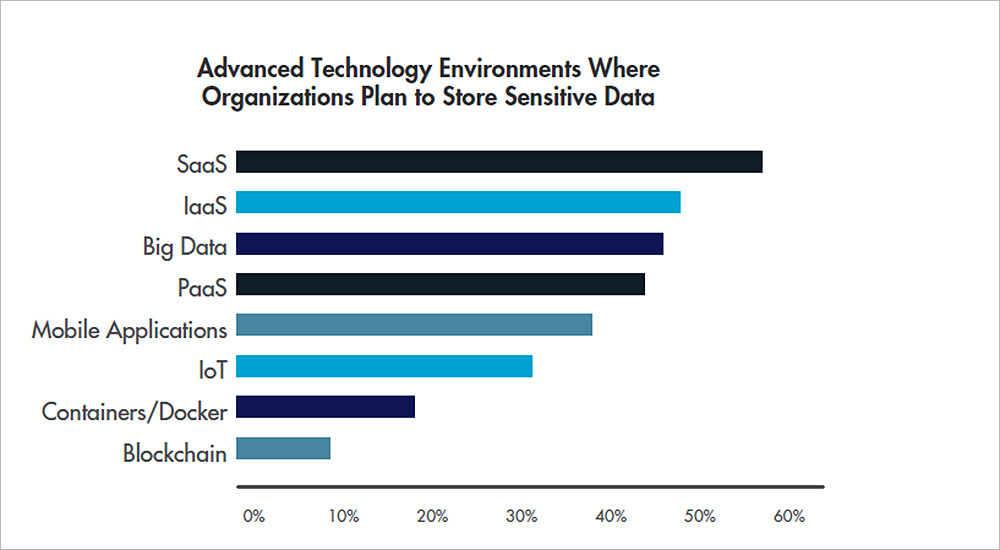
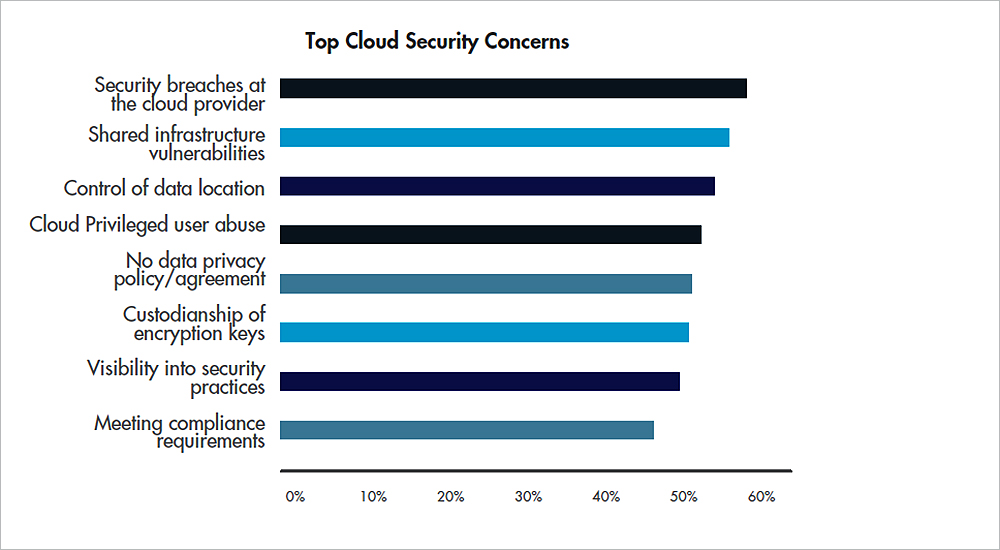
In this age of the cloud and SaaS enterprise deployments, more and more enterprise data is being created, transported, processed and stored outside corporate network boundaries, making traditional perimeter-based security controls and legacy network and endpoint protection solutions increasingly less relevant.
Other new, popular technologies also bring added security challenges. For example, nearly 40% of respondents are using Docker containers for production applications. At the same time, 47% cite security as the top barrier to broader Docker container adoption.
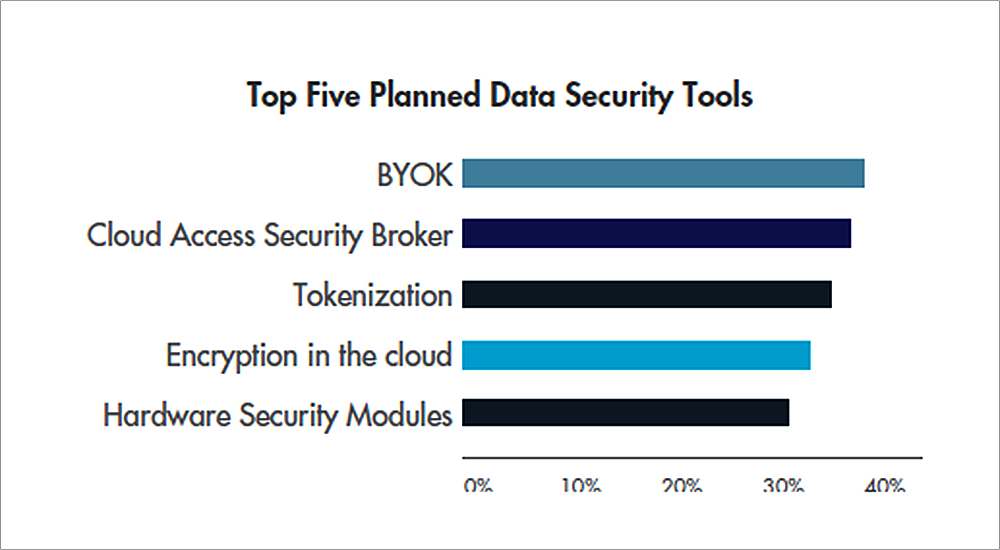
Peter Galvin, Vice President of Strategy, Thales e-Security says: “Enterprises must inevitably confront an increasingly complicated threat landscape. Our world, which now includes the cloud, big data, the IoT and Docker, calls for robust IT security strategies that protect data in all its forms, at rest, in motion and in use. Businesses need to invest in privacy-by-design defense mechanisms – such as encryption – to protect valuable data and intellectual property and view security as a business enabler that facilitates digital initiatives and builds trust between partners and customers.”
Click below to share this article